1. For perfectly price inelastic supply
supply determines price solely.
demand determines price solely.
only a government can set the price.
either supply or demand may set the price.
2. For Matthew, the marginal utility of the 9th soda in a day is positive and the marginal utility of the 10th soda in a day is zero. This
implies that Matthew's demand curve for sodas per day will become upward sloping at 10 sodas per day.
is impossible because each additional unit of consumption of any good must provide positive marginal utility.
implies that at a zero price Matthew's demand curve will intersect the quantity axis at 10.
implies that Matthew maximizes utility by consuming 9 sodas per day.
3. Jane has $500 a Week to spend on clothing and food. The price of clothing is $25 and the price of food is $10. Jane spends her entire income when she purchases ________ units of clothing and ________ units of food.
10; 10
25; 5
12; 20
16; 8
4.Michael Dell was the first individual who sold computers by mail order. The company founded by Dell is now one of the largest and most successful computer companies in the United States. Michael Dell would be classified as a(n)
entrepreneur.
opportunist.
monopolist.
socialist.
5. Demand determines price entirely when
demand is downward sloping.
demand is perfectly inelastic.
supply is perfectly inelastic.
supply is perfectly elastic.
6. As an individual consumes more of a product within a given period of time, it is likely that each additional unit consumed will yield
successively less satisfaction.
successively more satisfaction.
the same amount of satisfaction.
less satisfaction for a while and then start to add more satisfaction.
7. When there are more substitutes for a product, the ________ for the product is ________.
demand; less price elastic
demand; more price elastic
income elasticity; greater
income elasticity; smaller
8. A price change would have the largest income effect on a
magazine.
desktop computer.
piece of clothing.
car.
9. If the demand for sardines increases as income decreases, sardines are a(n)
normal good.
inferior good.
substitute good.
complementary good.
10. Jane has $500 a Week to spend on clothing and food. The price of clothing is $25 and the price of food is $10. The clothing and food pairs in Jane's choice set include ________ units of clothing and ________ units of food.
50; 50
20; 50
15; 25
8; 30
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"



1 For Perfectly Price Inelastic Supply Supply Determines Price Solely Demand Determi 3079527
/in Uncategorized /by developer1. For perfectly price inelastic supply
supply determines price solely.
demand determines price solely.
only a government can set the price.
either supply or demand may set the price.
2. For Matthew, the marginal utility of the 9th soda in a day is positive and the marginal utility of the 10th soda in a day is zero. This
implies that Matthew's demand curve for sodas per day will become upward sloping at 10 sodas per day.
is impossible because each additional unit of consumption of any good must provide positive marginal utility.
implies that at a zero price Matthew's demand curve will intersect the quantity axis at 10.
implies that Matthew maximizes utility by consuming 9 sodas per day.
3. Jane has $500 a Week to spend on clothing and food. The price of clothing is $25 and the price of food is $10. Jane spends her entire income when she purchases ________ units of clothing and ________ units of food.
10; 10
25; 5
12; 20
16; 8
4.Michael Dell was the first individual who sold computers by mail order. The company founded by Dell is now one of the largest and most successful computer companies in the United States. Michael Dell would be classified as a(n)
entrepreneur.
opportunist.
monopolist.
socialist.
5. Demand determines price entirely when
demand is downward sloping.
demand is perfectly inelastic.
supply is perfectly inelastic.
supply is perfectly elastic.
6. As an individual consumes more of a product within a given period of time, it is likely that each additional unit consumed will yield
successively less satisfaction.
successively more satisfaction.
the same amount of satisfaction.
less satisfaction for a while and then start to add more satisfaction.
7. When there are more substitutes for a product, the ________ for the product is ________.
demand; less price elastic
demand; more price elastic
income elasticity; greater
income elasticity; smaller
8. A price change would have the largest income effect on a
magazine.
desktop computer.
piece of clothing.
car.
9. If the demand for sardines increases as income decreases, sardines are a(n)
normal good.
inferior good.
substitute good.
complementary good.
10. Jane has $500 a Week to spend on clothing and food. The price of clothing is $25 and the price of food is $10. The clothing and food pairs in Jane's choice set include ________ units of clothing and ________ units of food.
50; 50
20; 50
15; 25
8; 30
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 Formal Decision Making Process By Which Large Organization Buy Services And Produc 2846873
/in Uncategorized /by developer1.Formal decision making process by which large organization buy services and products is classified as A.organizational buying B. large buying C.small buying D. procedure buying 2. Deciders and buyers in companies are classified as A.evaluators B.approvers C.buyers D.selectors 3.Business markets buy phases, include A.proposal solicitation B.product specification C.order-routine specification D.all of the above 4.Purchasing agents of companies in business markets dominate the A.buyer selection B.trial supplier?s C.product components D.supplier selection 5. Administrator who assists in selection and deselection of purchasing goods and services by screening information about products are A.purchasing agents B.system agents C.evaluation agents D.awareness agents
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 For The Truss Shown A 4 M B 3 5 M C 5m A Use Method Of Joints To Solve For Interna 2715163
/in Uncategorized /by developer1. For the truss shown, a = 4 m, b = 3.5 m, c = 5m
a) Use method of joints to solve for internal forces in DJ and JU.Consider the internal force at TI equal to 1.2 kN, COMPRESSION.
b) Use method of sections to solve for internal forces in WX and WL. Consider the force in member TU equal to 2. kN, TENSION.
Attachments:
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 From Scenario 1 Evaluate The Technology Proposed By Shawn Paschal What Is Your Rec 3079468
/in Uncategorized /by developer1. From Scenario 1, evaluate the technology proposed by Shawn Paschal. What is your recommendation on the adoption of this technology? Explain your reasoning.
2. From Scenario 1, what do you recommend to King Fisher regarding changing their 30 day collection period? Explain your reasoning.
3. From Scenario 2, what are your recommendations on the investment project? Explain your reasoning.
4. From Scenario 2, what are your recommendations for investment in the new technology?
5. From Scenario 3, evaluate King Fisher's target capital structure. What are your recommendations? Consider the impact of taxes and explain your reasoning.
save as a word doc
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 Free Flow Products The Largest Wholesaler In The Area Refuses To Sell Its Pr 2803742
/in Uncategorized /by developer1-Free Flow Products, the largest wholesaler in the area, refuses to sell its products to Papa Gene, Inc., a small retailer. Under antitrust law, this is
2- fran and wally do business as partners in Laugh Riot. for federal income tax purposes, Laugh riot would be treated as
3- which of the following demonstrates permanent legal residency in US?
4- under antitrust law, the reasonableness of an exclusive-dealing contract is never a justifiable defense.
Document Preview:
1-Free Flow Products, the largest wholesaler in the area, refuses to sell its products to Papa Gene, Inc., a small retailer. Under antitrust law, this is Not a violation Subject to the rule of reason A deceptive practice A per se violation 2- fran and wally do business as partners in Laugh Riot. for federal income tax purposes, Laugh riot would be treated as A partnership by estoppel A natural person A tax-paying entity A pass-through entity 3- which of the following demonstrates permanent legal residency in US? I-551 Alien Registration Receipt I-9 verification H-IB visa L visa 4- under antitrust law, the reasonableness of an exclusive-dealing contract is never a justifiable defense. True Fales 5- As presented in class in the movie clip from inside job, leading up to the financial crisis of 2008 investment banks bundled risky home loans into securities called_______ that were then sold to investors. Subprime mortgage Credit default swaps Collateralized debt obligations Adjustable rate mortgage 6- wizbang widgets requires its employees to have at least 2 years of college, claiming a definite connection between 2 years of college and job performance. In a suit against wizbang under the civil rights act of 1964, the plaintiff shows that this job requirements discriminates against a protected class. Wizbang can offer No defense An affirmative action defense A bona fide occupational qualification defense A business necessity 7- Under the business judgment rule a director or officer can be held legally liable for bad (mistaken) business decisions. A-True (Business Judgment Rule: A rule that immunizes corporate management from liability for actions that are undertaken in good faith and are within both the power of the) B-Fales 8- the civil rights act of 1964 prohibits job discrimination against minority and majority group individuals, such as white males True false 9- three small restaurant suppliers with little market power decide together that they…
Attachments:
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 Give 3 Examples Of Nanomaterials That Differ In Properties When At The Nanoscale V 854473
/in Uncategorized /by developer1. Give 3 examples of nanomaterials that differ in properties when at the nanoscale vs. bulk. 2. Define the pros and cons of top-down vs. bottom-up production processes. 3. Give 3 examples of (physical and/or chemical) processes that can be used to produce nanoscale powders. 4. What are the methods that can be used to stabilise colloidal nano-suspensions?
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 From The E Activity Compare And Contrast The Different Approaches Used For Acl Str 1582357
/in Uncategorized /by developer1) From the e-Activity, compare and contrast the different approaches used for ACL structure and the implications of “deny all” or “allow all” sequence placement.2) Discuss how NTFS permissions can be used to configure Website security and the basic concepts related to configuring certificates.3) Imagine that you are managing 20 Websites on a single Windows 2008 Web Server. For security, reliability, and performance reasons, you need to prevent problems occurring in one Web application from causing issues with others. One of the Web applications was originally designed for IIS 6.0.IIS7 on a single server can host multiple separate Websites simultaneously using one of these three binding solutions: IP address hosting, port number hosting, and host header hosting. Select the method that you would use if your main concern is securing your Website. Explain your selection.Analyze how you can minimize the risks associated with Web application defects affecting other Web applications. Choose one method by which you can support the IIS 6.0 application
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 Give A Possible Use Of Port Migration In Chorus 2 It Is Possible To Send A Message 2620566
/in Uncategorized /by developer1. Give a possible use of port migration in Chorus.
2. It is possible to send a message to a port group in Chorus. Does the message go to all the ports in the group, or to a randomly selected port?
3. Chorus has explicit calls to create and delete ports, but only a call for creating port groups (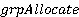 ). Make an educated guess as to why there is no grpDelete.
). Make an educated guess as to why there is no grpDelete.
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 Give An Example Of A Trading Economy Of Scale 2 Give Two Examples Of Diseconomies 2625116
/in Uncategorized /by developer1. Give an example of a trading economy of scale.
2. Give two examples of diseconomies of scale.
3. Why has the small-firm sector of the economy grown in the 1980s and 1990s?
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"
1 Give A Way To Multiply Two Complex Numbers Together Using Fewer Than Four Integer 2538349
/in Uncategorized /by developer1. Give a way to multiply two complex numbers together using fewer than four integer multiplication operations.
2. How much storage would be used by the FFT' if we didn't circumvent the storage-management problem with the perfect shuffle?
"Looking for a Similar Assignment? Get Expert Help at an Amazing Discount!"